Google researchers said they uncovered a Kremlin-backed operation targeting recruits for the Ukrainian military with information-stealing malware for Windows and Android devices.
The malware, spread primarily through posts on Telegram, came from a persona on that platform known as "Civil Defense." Posts on the @civildefense_com_ua telegram channel and the accompanying civildefense[.]com.ua website claimed to provide potential conscripts with free software for finding user-sourced locations of Ukrainian military recruiters. In fact, the software, available for both Windows and Android, installed infostealers. Google tracks the Kremlin-aligned threat group as UNC5812.
Dual espionage and influence campaign
"The ultimate aim of the campaign is to have victims navigate to the UNC5812-controlled 'Civil Defense' website, which advertises several different software programs for different operating systems," Google researchers wrote. "When installed, these programs result in the download of various commodity malware families."
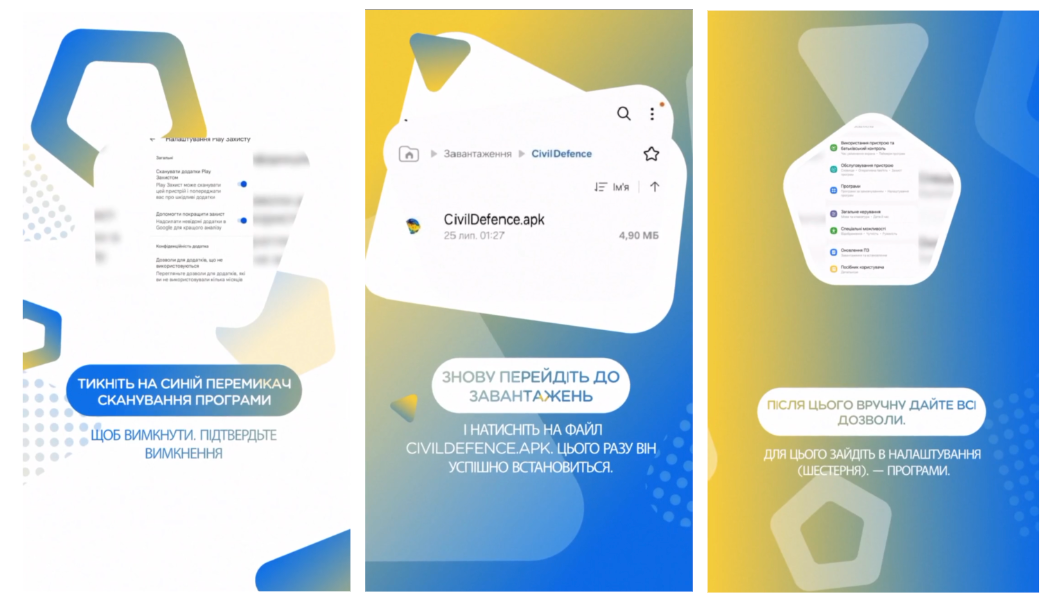
The Android versions used social engineering to trick users into turning off Play Protect, a Google service that automatically scans devices for malware, whether from Play or third-party sources. During installation, the app also provided reassurances that the scary system privileges being requested were necessary to protect the safety of users.
An FAQ on the website also contained a "strained" justification for the Android app not being available in Play, but rather only as a side-load downloaded from the site. The justification is designed to preempt common security advice that Android users steer clear of sideloaded apps and obtain apps solely from Play.
The campaigns for Windows and Android relied on off-the-shelf infostealers. The Android infostealer is a variant of CraxsRat, a package that implements many backdoor functionalities typically found in Android backdoors.
The Windows malware, meanwhile, used a custom version of Pronsis Loader, which was discovered last month by security firm Trustwave, to install PureStealer, available for sale online for $150 a month or $699 for a lifetime license.
The Civil Defense website also advertises support for macOS and iOS, but versions for those platforms weren't available at the time of analysis.
The Google researchers wrote:



 Loading comments...
Loading comments...
